I finally watched K9 and Company. And I have questions.
If you’re unfamiliar with it, K9 and Company was a single 50 minute TV show made in 1981, a spin-off from Doctor Who that was intended to be a series, making companion Sarah Jane Smith, played by Elisabeth Sladen, into the lead character, fighting evil with K9, the robot dog companion she’d never worked with in Doctor Who itself. The series was never made, although a similar concept was eventually to resurface many years later in 2007 on the CBBC channel as The Sarah Jane Adventures.
I’d been aware of the programme, mainly because it’s possibly best known for having one of the worst title sequences ever made, much derided and parodied. But the show itself… I wasn’t prepared for it. It was nothing like I expected. I can see why a series was never commissioned, but not for any of the reasons I might have assumed. It left me utterly discombobulated, needing to watch it again. And write this. (It contains spoilers, so if you’ve not seen it, go and watch it before reading this).
I’ll skip over the music, because I don’t want to go there, and also skip over just how bad the titles are, but I want to talk about tone. A lot of my astonishment with K9 and Company is about tone.
From the titles you’d assume this is going to be a bit of a crazy, kooky knock-about adventure, perhaps a little bit cosy. Sarah Jane drives around in her soft-top Mini Metro, getting into scrapes, jogging in Pineapple-era dancewear, knocking back the odd glass of white wine outside a pub whilst filing copy on her portable typewriter (let’s hope it’s not a Sam Smiths pub with technology like that) and solving mysteries with K9, her plastic pal who’s fun to be with.
Then the show starts. And tonally, we are not in Croydon anymore. We’re not even in Doctor Who, it’s like we’re in something more like a 1970s ATV Thriller, or an episode of Tales of the Unexpected. Sarah Jane has pitched up in her Aunt Lavinia’s massive country house in the Cotswolds. VT interiors, grown-ups talking in grown-up ways in drawing rooms. Juno Baker looks like she has pampas grass in her front garden. The pace is slow. The whole thing feels a bit dated even for 1981, and it certainly does not feel like a show made for children.
Things seem to be getting back on track when Colin Jeavons appears, playing the gardener. I love Colin Jeavons, and I feel like he was a staple of children’s film and TV when I was growing up, or grown-up programmes that appealed to kids like me, usually cast as small-time villains.
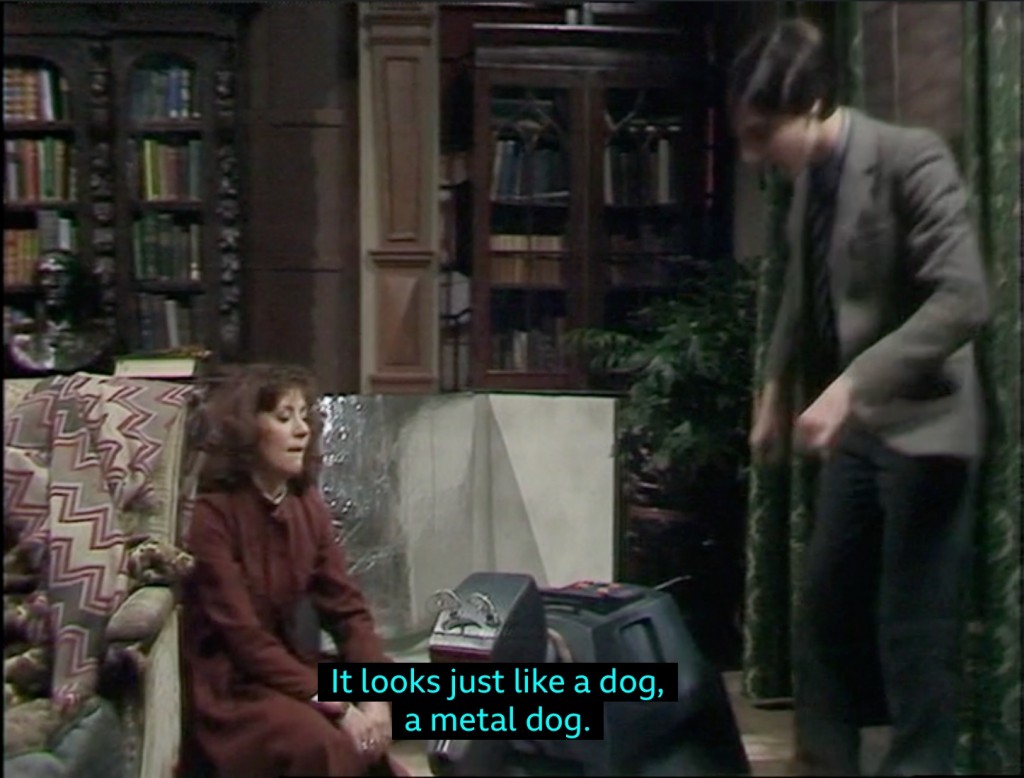
The unboxing of K9 by Sarah Jane and her aunt’s ward Brendan also feels more appropriate. The very existence of a character being a ward seems to give us some kind of link into the long history of wintertime children’s TV adaptations of classic stories.
However, the mystery as it unfolds takes us, for me at least, somewhere utterly unexpected. Aunt Lavinia has disappeared after writing a letter to the local newspaper about witchcraft being practised in the area. Sarah Jane, Brendan and K9 uncover a plot, of course, but not some cosy scheme. Oh no. It’s a full-blown Hammer / folk horror satanic cult, comprising all the local dignitaries, who hold rituals by night, in masks in scenes that literally appear to be straight out of Hot Fuzz. If that’s not scary enough, they then kidnap Brendan and decide to make him a human sacrifice.
So, who on earth was this aimed at? Let’s look at the evidence:
The titles look like a low-end kids’ show. The programme itself is filmed and paced like a late 70s adult drama. Its main plot concerned a satanic cult and human sacrifice. And it was broadcast to millions on BBC1 at 5.45pm on Monday 28th Dec 1981, then repeated a year later on BBC2 on Christmas Eve 1982 at 5.40pm. Very mixed messages, possibly even so much so that it’s a bit on the nose even for someone like me from the ‘haunted generation.’
The other reason for my discombobulation is that, although I’ve heard of it, I don’t remember watching it at the time. Which is very odd. I was the right age for it in 1981, I was (and am) a fan of Doctor Who in general, and Sarah Jane Smith in particular. How could I have missed both showings? I was in the habit at the time of circling programmes I wanted to watch in biro in the Christmas double-length Radio Times, how could it have eluded me? We may even have, just, had a VCR then, but could a schedule clash, or just tea-time have been the reason? Or is there some sinister reason where I had amazing adventures in time and space just after seeing it, causing me to have my memory erased before being dumped back into North Somerset on Christmas day 1982? Is that why there is strange satanic incantations (ok, Latin body text) on the web site of one of the locations?
There is another possibility. One of my older brothers was friends with Bob Baker and Dave Martin, who created K9 for ‘The Invisible Enemy’ Doctor Who story in 1977. I’m away from home right now and can’t check Bob Baker’s autobiography, which my brother worked on, but I wonder if there was some beef over Bob & Dave not being involved in K9 and Company and I was encouraged not to watch it? Or maybe it’s just that my holographic memory circuits are failing, mistress…
K9 and Company is currently on the BBC iPlayer.